Recently there has been a rise and fall of several penny auction sites boasting about selling genuine high-demand items at massive discounts off recommended retail prices. But all is not what it seems.
The secret to this scam is that you must pay money every time you make a bid!
And every time a bid is made, the timer for the auction increases a little bit, usually by about 10 seconds. So you have a $1000 camera with a bid for $150 and its got 6 seconds left, but nope, someone else makes a bid and extends the timer by 12 seconds or so, and then another, and another and this can go on for hours.
How much each bid costs varies, but usually they will front-bill your credit card (when you signup) for 200 bids for, say for the sake of argument $100. Many people often complain that the charge to their credit card is under-played and not obvious until its to late. Usually, getting refunds from Penny Auction operators is like trying to get blood out of a stone. (Although this practise itself is not a scam; it is definitely misleading).
Now is where the trouble starts.
The thing that most people don’t understand (and where the scam kicks in) is that penny auction operators are allowed to shill their own auction’s bids. They typically do this because;
- The price is too low
- If not enough people have big on the item
In other words, if the money paid by either the actual bid, or the charges made to the sum of people bidding is LESS than the cost of the item, the site will simply start bidding on its own behalf to push up the price (and extended the duration).
The other dangerous part of the penny auction is that the site operators are allowed to sell your browsing habits and personal information with third-parties, often with those that helps the operator perform “services”.
So with every bid effectively being charged to a credit card; each individual bid (with the obvious exception of the shill bids) subsidises the price of the equipment for the person who eventually wins the item and whom musty pay not only the price they bid, but also for each bid they made.
Sure, some people do actually win very cheap items. But for every individual auction there are several losers making up the difference in price (and who receive nothing). And since the auctioneer can bid against you, no item need actually be sold until the auction site has made a huge profit on that “cheap” item.
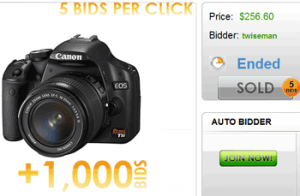
Fun Facts from a “Swipe Auctions” example:
By the time the auction ended (5 hours later than the first image at the top), the camera in the Swipe Auctions auction pictured had had another 13,105 BIDS!!
At using an EXTREMELY conservative estimate of 5 cents a bid, people still spent $1,283 on bids alone (probably closer to $2,500), and the guy who won had to buy the camera for $256 on top of whatever he spent on bidding.
Only 1 person won that camera auction, and only after spending several hundreds in bids.
Several people lost this auction and threw their money down the drain and wasted several hours of their lives.
There is no way to know if Swipe Auctions extended the auction superficially on their side in order to make more money (is it a coincidence that it ended so abruptly so early (11:00pm), but right after they cleared over $100 in bids (AT LEAST) over the MSRP of the camera?)
For the record, Swipe Auctions no longer exists (and they had actually launched dozens of ‘sister sites’- I have no idea if any of those are still in operation). But this article is written in the hopes that I can protect people from falling into these dodgy sites who aim to take your money and give you very little if nothing in return.